Table of Contents
The house has traditionally been the family’s most personal put. But initially the cell cellphone and now wise gadgets have entered that room. Their digital discussions mean that, often with out the users’ expertise, they share personal specifics about the household that had been earlier unachievable to acquire. Right until now, exploration on these devices focused on exterior hazards: is it attainable to entry a home digital camera from the world wide web? Is a wise speaker susceptible to eavesdropping? Right now, groundbreaking do the job by many universities and investigate centers has identified that beneath the superficial tranquil of a dwelling, there lurk lots of challenges.
“One of the greatest complications is the invasion of privateness,” suggests David Choffnes, professor at Northeastern University in Boston and one of the co-authors of the perform. “These weaknesses give attackers a distinct strategy of what is in your house, who is there, as perfectly as the place they are going and when. We identified that some applications acquire edge of this to gather data from residences, for functions that have absolutely nothing to do with their purpose. If our properties are our most non-public location, it appears like a really serious invasion of privacy to me,” he adds.
Choffnes and his staff at Northeastern established up a “living lab/condominium with about 100 devices,” dubbed Mon(IoT)r Lab, at their university. It is like a big get together, but with gadgets. In the lab, scientists from the college and other facilities research the complete selection of behaviors and interactions that manifest in between the products, from light bulbs and refrigerators to routers and speakers, which converse with every single other. This investigation also research all of their connections with applications, both equally individuals that regulate these devices and some others that Android users have on their cellular phones, and the two these who dwell in that residence and all those who stop by it. Apple’s atmosphere is significantly additional personal.
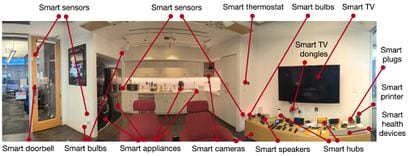
EL PAÍS has requested Google, which purchased Android in 2005 and has a line of good units, about this examine. A spokesperson responded: “We considerably appreciate the protection community’s study. We are consistently enhancing our security protections to support keep Android buyers protected.” The Android surroundings, thanks to its character and variety of actors, has a whole lot of troubles to prevail over.
“I never think men and women have the slightest concept that all products related to Wi-Fi talk to each other in some way. And that has implications,” states Juan Tapiador, professor at the Carlos III University and an additional co-creator of the research.
What type of info do these units share? They are not like the conversations or messages we send. The form of information that they share ranges from exceptional device addresses (MAC), serial numbers, versions of vulnerable protocols, or even names of distinct equipment these as “Joe’s speaker in the eating space.”
All this info, and the services to which they join, let numerous facts of our lives to be inferred, and could offer a digital fingerprint of our residence, which would let targeted assaults or surveillance. “The uncontrolled publicity of this info,” says Narseo Vallina-Rodríguez, researcher at Imdea Networks and co-author, “allows promoting solutions or spy applications to produce a electronic fingerprint of your dwelling that uniquely identifies it or can infer your revenue level and routines.” Not only that, if these devices scan for new information and facts often “they can infer who enters and leaves the house and your social constructions to check their activities by way of networks and gadgets,” provides the pro.
We do not absolutely recognize the risks
Buyers may possibly think that all this is not these kinds of a critical issue for the reason that the details does not seem to be so non-public. They tend to misunderstand the pitfalls included in collecting dozens of certain pieces of information about a household. For example, this info is captured by applications that we carry on our phones and they gather the serial number of the router or the name of the connection, which enables us to know the location (with no even accessing the device’s GPS). There are web pages the place Wi-Fis from all about the environment are mapped. If two mobile phones accessibility the same Wi-Fi, you not only know that they are shut, but also in which they are. If an application on the visitor’s cell scans how lots of intelligent products are there, and which ones, that knowledge can support estimate the domestic earnings of that dwelling.
“One of the issues that was most complicated for us to have an understanding of is that the instructive benefit of specialized information is from time to time complicated to forecast,” says Tapiador. The SSID, which is the title of the Wi-Fi community, is a very good illustration. When a cellular scans the accessible networks, the identify of all individuals nearby can be seen. “There are a lot of online companies that present you with geolocation information based mostly on that identify,” continues Tapiador.
A distinct example of the fearsome use of the mix of information that can be gathered many thanks to these equipment is presented by Vijay Prakash, a researcher at New York University, and co-creator of the review: “If a malicious actor abuses the information and facts that floats freely in sensible dwelling networks they can track a consumer throughout gadgets from many vendors. For illustration, if a destructive software normally takes fingerprints from several users’ good properties, and some of them visit the dwelling of one particular of the other buyers — let us simply call her Jane — with their cellphone on them, the software could infer Jane’s social associations and schedules in which other people take a look at her.” It need to be taken into account that this would not happen just at the time, but consistently.
The applications analyzed in the study experienced thousands and thousands of downloads that contained computer software that collects this type of information and facts. If an application has access to place details and scans Wi-Fi networks, it by now is aware of that all those networks are in that put: “This is crowdsourcing carried out by millions of people,” Tapiador carries on. “There are maps with people names from all more than the earth. When you convey to a person, ‘hey, this gentle bulb is picking up the SSID or MAC handle of the router’ it’s the exact as declaring, ‘this light-weight bulb is selecting up the location of your household.’” That is not the only challenge: “The question is what other associations they can construct from there. Allowing you to have accessibility to targeted visitors created by your units can have unanticipated penalties,” he claims.
Devoid of legal permissions
A lot of of these illustrations are not authorized, but the Android atmosphere is a jungle: “These practices have several implications, because they typically happen without any form of consumer consent, and delicate info these as geolocation or products and customers (info secured by the Basic Info Security Regulation) is also received,” says Vallina-Rodríguez.
This is an illustration of the elaborate dance of conversations that gadgets have in a household, as explained in the analysis: “Six [of home device] purposes transmit the [unique MAC] addresses of devices to the cloud, and the recipients are their possess domains [for example, Alexa] or third-occasion suppliers this sort of as Tuya, (a [home device] platform supplier, centered in China), and Amplitude, which is an analytics company.”
To a human, this mix of details may possibly appear too much to handle and unbearable. But for equipment it is their day by day get the job done. Past hypothetical stability pitfalls, this facts feeds the huge, dim equipment of worldwide marketing and promoting, also called “commercial surveillance.” At the minute it is not going on, but just as we obtain individualized promotion on cell telephones, the marketplace could discover our household and tailor the advertising to our economic and spouse and children predicaments: what is a lot easier than identifying when a pair has separated or how significantly the pal who has arrive to your birthday party earns?
“Just as many pages build a fingerprint of the consumer so they can identify them between periods even if they delete their cookies,” says Tapiador, “we observed that it is attainable to do the identical for a dwelling making use of the equipment. It is a theoretical observation in the feeling that personalization aimed at distinct homes is not permitted now, but the risk that it can be completed continue to exists,” he adds.
Sign up for our weekly newsletter to get more English-language information protection from EL PAÍS United states of america Edition






More Stories
Revitalize Your Building’s Exterior: The Magic of Softwashing
Four Key Focal Points for Efficient House Cleaning in St. Petersburg, FL
Are your home’s clever products leaking non-public information? Calgary researcher set to discover out